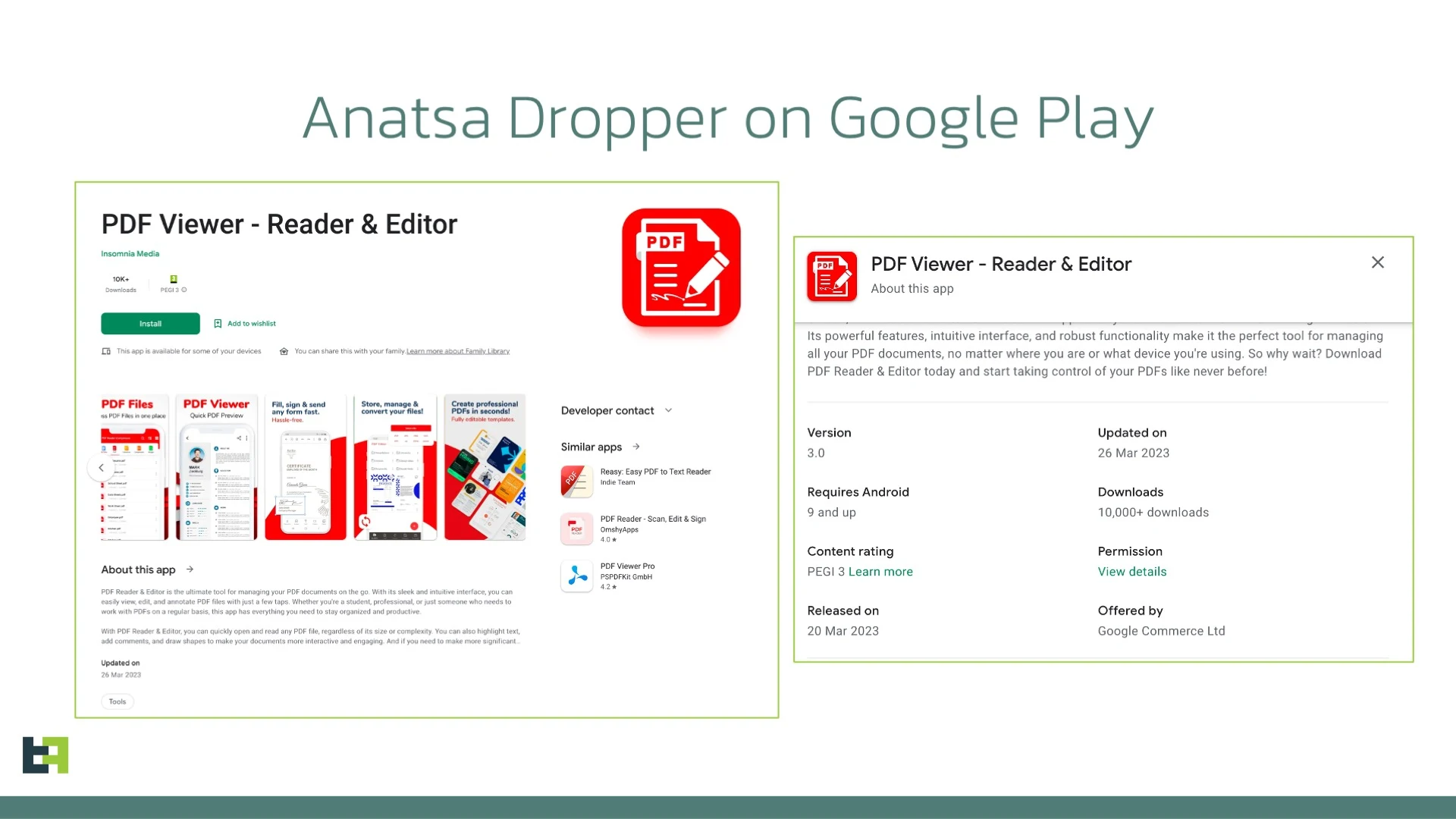
A new warning has been issued by security experts regarding the harms linked to a new Android banking trojan called Anatsa.
Researchers claim the trojan has been revamped with some additional features and actions that target more banking applications.
As per security researchers this mobile malware initiatives have been out and about since the month of March of 2023. And clients based in Switzerland, the US, Germany, Austria, and the UK were affected.
It was similar to a campaign that arose in the past, around two years back, that saw the malware being installed nearly 300k times. This is also where hackers involved started to use malicious platforms that received hosting through the Play Store so it could infect those having Android devices that were susceptible to attack.
This new version of the trojan called Anatsa was highlighted by experts at ThreatFabric. They showcased through new reports how it would take over more than 600 banking platforms while committing fraud across susceptible devices.
It’s appalling how a leading number of banks were involved in this malicious scheme such as Capital One, Navy Federal, and several other big names in the industry. Therefore, this is one of the leading reasons why such threats are being taken so seriously across the board.
The reports have boldly mentioned how individuals need to get rid of the apps at an urgent notice and they’ve even listed those down for user ease and convenience. They’re not only taking over but draining people’s financial accounts.
Therefore, if anybody has such apps installed on an Android device, it’s always recommended that they delete it with immediate effect.
The list includes names such as PDF Reader, PDF Editor, All Document Reader, and All Document Reader With Editor. Thankfully, all the apps highlighted as dangerous were removed but it’s still recommended that users get rid of them on a manual basis if they’re stored across a smartphone.
Other reports spoke about how we witnessed a hiatus comprising six months after which the cybercriminals involved with this banking trojan started to lay down another damaging campaign involving poor advertising to market such apps that drop such trojans.
Similar to other campaigns of the past that included this banking trojan, this particular one utilizes malicious apps that appear like they’re PDF editors. Interestingly, when such apps were sent to Google, they failed to entail damaging malware.
With time, it was added to Google’s Play Store which passed through major security checks.
So how exactly does this ordeal work? After getting installed across Android devices, they grab a hold of sensitive data like credit card information and bank account details. This occurs with the help of overlays that pop up at the top after getting launched.
The trojan uses this data to carry out fraud on devices by rolling out one banking app and making transactions across the victims. Hence, it really does end up saving a lot of time for hackers and increases success rates without anyone even knowing.
After funds are taken in, they’re transformed into the likes of cryptocurrency. But how does one stay safe from such ordeals, to begin with?
Staying safe is no longer an easy task in today’s world. For starters, experts recommend restricting the figure for apps on a device. Moreover, even those that appear innocent may entail malware or can be included at some point later in time. And that’s when you need to ask if you need any certain app or not, right before making an installation.
Google admits it plays a crucial role in terms of checking apps put across its Play Store. It ensures those having malware get removed while bad ones may end up slipping through.
Read next: 66% of Executives Lost Customers Due to Cyber Attacks in the Past 2 Years
Researchers claim the trojan has been revamped with some additional features and actions that target more banking applications.
As per security researchers this mobile malware initiatives have been out and about since the month of March of 2023. And clients based in Switzerland, the US, Germany, Austria, and the UK were affected.
It was similar to a campaign that arose in the past, around two years back, that saw the malware being installed nearly 300k times. This is also where hackers involved started to use malicious platforms that received hosting through the Play Store so it could infect those having Android devices that were susceptible to attack.
This new version of the trojan called Anatsa was highlighted by experts at ThreatFabric. They showcased through new reports how it would take over more than 600 banking platforms while committing fraud across susceptible devices.
It’s appalling how a leading number of banks were involved in this malicious scheme such as Capital One, Navy Federal, and several other big names in the industry. Therefore, this is one of the leading reasons why such threats are being taken so seriously across the board.
The reports have boldly mentioned how individuals need to get rid of the apps at an urgent notice and they’ve even listed those down for user ease and convenience. They’re not only taking over but draining people’s financial accounts.
Therefore, if anybody has such apps installed on an Android device, it’s always recommended that they delete it with immediate effect.
The list includes names such as PDF Reader, PDF Editor, All Document Reader, and All Document Reader With Editor. Thankfully, all the apps highlighted as dangerous were removed but it’s still recommended that users get rid of them on a manual basis if they’re stored across a smartphone.
Other reports spoke about how we witnessed a hiatus comprising six months after which the cybercriminals involved with this banking trojan started to lay down another damaging campaign involving poor advertising to market such apps that drop such trojans.
Similar to other campaigns of the past that included this banking trojan, this particular one utilizes malicious apps that appear like they’re PDF editors. Interestingly, when such apps were sent to Google, they failed to entail damaging malware.
With time, it was added to Google’s Play Store which passed through major security checks.
So how exactly does this ordeal work? After getting installed across Android devices, they grab a hold of sensitive data like credit card information and bank account details. This occurs with the help of overlays that pop up at the top after getting launched.
The trojan uses this data to carry out fraud on devices by rolling out one banking app and making transactions across the victims. Hence, it really does end up saving a lot of time for hackers and increases success rates without anyone even knowing.
After funds are taken in, they’re transformed into the likes of cryptocurrency. But how does one stay safe from such ordeals, to begin with?
Staying safe is no longer an easy task in today’s world. For starters, experts recommend restricting the figure for apps on a device. Moreover, even those that appear innocent may entail malware or can be included at some point later in time. And that’s when you need to ask if you need any certain app or not, right before making an installation.
Google admits it plays a crucial role in terms of checking apps put across its Play Store. It ensures those having malware get removed while bad ones may end up slipping through.
Read next: 66% of Executives Lost Customers Due to Cyber Attacks in the Past 2 Years