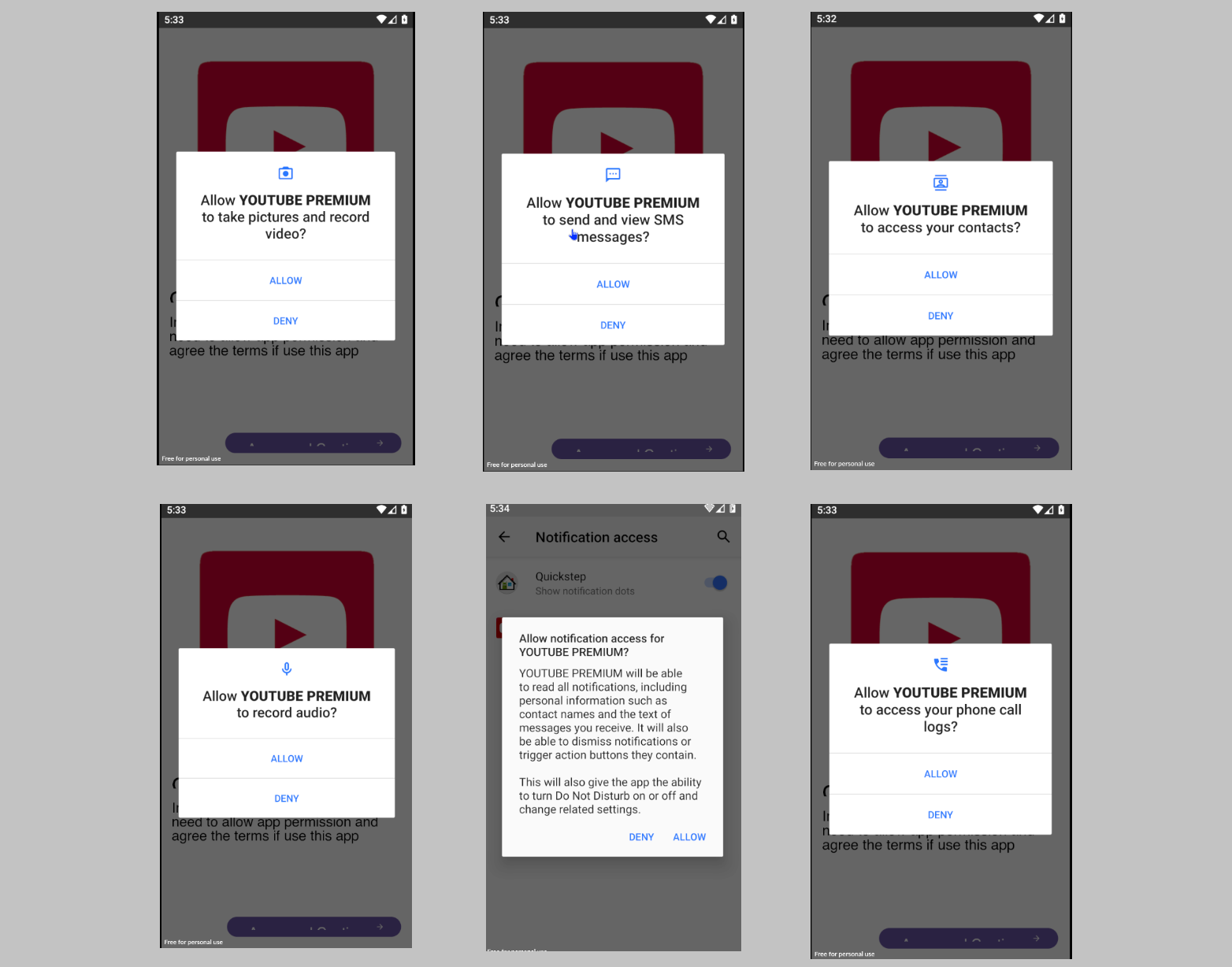
With the ever-changing digital landscape, cybercriminals are constantly adapting their tactics to exploit vulnerabilities. Recently, security experts have raised an alarm regarding dangerous Android malware that presents a grave risk to users. This malware, referred to as DogeRAT (Remote Access Trojan), was discovered by CloudSEK's cybersecurity researchers. Its functionalities encompass a wide range of malicious activities, including unauthorized access to personal data like contacts and messages, as well as the theft of sensitive banking information. Furthermore, it has the capability to seize control of compromised devices, distribute spam, manipulate files, and even compromise the device's camera for nefarious purposes.
The alarming aspect of this malware lies in its capacity to disguise itself as a genuine application. Malicious actors are spreading it across social media and messaging platforms, specifically targeting unsuspecting users who are enticed by seemingly harmless apps, including popular ones such as games, productivity tools, and entertainment platforms like YouTube and Netflix. It is worth noting that this malware is not available on the official Google Play Store, which amplifies the challenge of identifying and evading it.
The team at CloudSEK has made an important finding regarding the promotion of this malware. The creators of the malicious software have taken to Telegram, the widely-used messaging platform to actively advertise it. What's more, they have developed a premium version of the malware that boasts enhanced capabilities like screen capture, image theft, and keylogging. Interested individuals can obtain this upgraded version for nearly $30. To further entice potential users, the malware's developers have established a GitHub page where they provide comprehensive video tutorials and explanations to guide individuals on how to use the malware effectively.
The precise extent of device infections caused by this malware remains undisclosed. Nevertheless, it is crucial to emphasize that users must provide the malware with extensive permissions in order for it to function as intended. These permissions encompass various areas, such as SMS messages, audio recordings, call logs, photos, and media files. CloudSEK strongly advises users to exercise caution during the app download process as relying solely on the reputation of the Google Play Store is inadequate. Threat actors have demonstrated their ability to infiltrate the platform and manipulate scores and reviews, making it imperative for users to remain extra vigilant, especially when acquiring .apk files from third-party sources, which pose a heightened risk.
In an era of increasingly sophisticated cyber threats, users must remain diligent and proactive in safeguarding their devices and personal information. Implementing security best practices, such as regularly updating software, avoiding suspicious app downloads, and practicing good digital hygiene, is crucial to minimizing the risk of falling victim to such malware attacks.
As the cybersecurity landscape continues to evolve, it is imperative for users to stay informed and exercise caution when navigating the digital realm. By remaining vigilant and adopting robust security measures, individuals can better protect themselves against the ever-present threat of malware and cybercrime.
Read next: The Quest for Public Attention Intensifies as AI vs Bitcoin Search Battle Continues
The alarming aspect of this malware lies in its capacity to disguise itself as a genuine application. Malicious actors are spreading it across social media and messaging platforms, specifically targeting unsuspecting users who are enticed by seemingly harmless apps, including popular ones such as games, productivity tools, and entertainment platforms like YouTube and Netflix. It is worth noting that this malware is not available on the official Google Play Store, which amplifies the challenge of identifying and evading it.
The team at CloudSEK has made an important finding regarding the promotion of this malware. The creators of the malicious software have taken to Telegram, the widely-used messaging platform to actively advertise it. What's more, they have developed a premium version of the malware that boasts enhanced capabilities like screen capture, image theft, and keylogging. Interested individuals can obtain this upgraded version for nearly $30. To further entice potential users, the malware's developers have established a GitHub page where they provide comprehensive video tutorials and explanations to guide individuals on how to use the malware effectively.
The precise extent of device infections caused by this malware remains undisclosed. Nevertheless, it is crucial to emphasize that users must provide the malware with extensive permissions in order for it to function as intended. These permissions encompass various areas, such as SMS messages, audio recordings, call logs, photos, and media files. CloudSEK strongly advises users to exercise caution during the app download process as relying solely on the reputation of the Google Play Store is inadequate. Threat actors have demonstrated their ability to infiltrate the platform and manipulate scores and reviews, making it imperative for users to remain extra vigilant, especially when acquiring .apk files from third-party sources, which pose a heightened risk.
In an era of increasingly sophisticated cyber threats, users must remain diligent and proactive in safeguarding their devices and personal information. Implementing security best practices, such as regularly updating software, avoiding suspicious app downloads, and practicing good digital hygiene, is crucial to minimizing the risk of falling victim to such malware attacks.
As the cybersecurity landscape continues to evolve, it is imperative for users to stay informed and exercise caution when navigating the digital realm. By remaining vigilant and adopting robust security measures, individuals can better protect themselves against the ever-present threat of malware and cybercrime.
Read next: The Quest for Public Attention Intensifies as AI vs Bitcoin Search Battle Continues