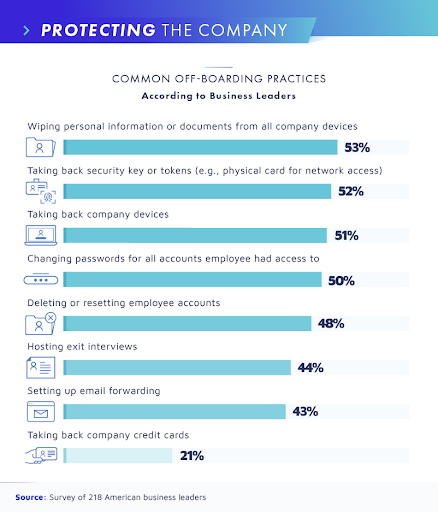
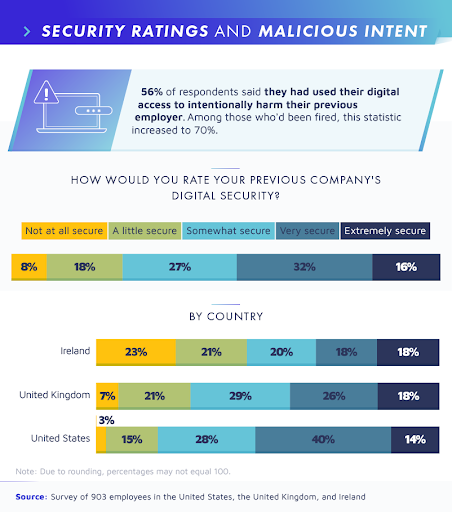
A survey conducted by Beyond Identity reveals that 83% of retired employees of a firm have used their business’ private information, confidential data, and accounts, leading to a company being vulnerable to threats.
Nowadays, switching from one job to another has become more common. Once people find a job, they start to shift from there due to low pay or any other reason. It has been indicated in a report that about 56% of Company workers have access to personal accounts, passwords, and other digital data of a departed employer, and these workers are found to be involved in malicious acts thus, harming the privacy of companies. Likewise, poor off-boarding terms between the employee and a company boss led to threats on both parties. Ex-workers use the company’s financial accounts and exploit the business by stealing clients’ contact information in 25% of the cases.
When an employee signs resignation, documents, and application is submitted to HR in 31% of the usual cases. Company’s accessed accounts and provided email accounts access are supposed to be returned to the company according to the terms and conditions. But what happens is that retired employees still have access to the Company’s software accounts and important files in up to 31% of cases. Former workers hijack the company’s website and steal the payrolls system without authorization.
All of these off-boarding practices need to be revised and proper terms should be maintained by the company and the leaving employer upon resignation or termination. These activities aren’t good at all. It harms one’s reputation and leads to business losses and leaking out of in-depth information of a firm or a worker, exploiting one’s image in the public. Some practices can be done to prevent this:
1. Strict security administration practices should be observed while resigning.
2. A company should clear the commits code.
3. A company should create awareness among the workers to mention any suspicious acts if noticed.
4. They should remove the dormant accounts and enable 2-factor authentication.
The major focus should be on the security policy. During off-boarding, employers must hand over all the digital accounts and resources of the company to the Information Technology department and seek necessary practices to ensure that they haven’t got anything illegally along with them. Similarly, the company must ensure the worker that his personal information and dormant accounts are completely signed-out from the devices.

Read next: The Majority of Cyber Attacks in 2021 Targeted Educational and Government Institutions
Nowadays, switching from one job to another has become more common. Once people find a job, they start to shift from there due to low pay or any other reason. It has been indicated in a report that about 56% of Company workers have access to personal accounts, passwords, and other digital data of a departed employer, and these workers are found to be involved in malicious acts thus, harming the privacy of companies. Likewise, poor off-boarding terms between the employee and a company boss led to threats on both parties. Ex-workers use the company’s financial accounts and exploit the business by stealing clients’ contact information in 25% of the cases.
When an employee signs resignation, documents, and application is submitted to HR in 31% of the usual cases. Company’s accessed accounts and provided email accounts access are supposed to be returned to the company according to the terms and conditions. But what happens is that retired employees still have access to the Company’s software accounts and important files in up to 31% of cases. Former workers hijack the company’s website and steal the payrolls system without authorization.
All of these off-boarding practices need to be revised and proper terms should be maintained by the company and the leaving employer upon resignation or termination. These activities aren’t good at all. It harms one’s reputation and leads to business losses and leaking out of in-depth information of a firm or a worker, exploiting one’s image in the public. Some practices can be done to prevent this:
1. Strict security administration practices should be observed while resigning.
2. A company should clear the commits code.
3. A company should create awareness among the workers to mention any suspicious acts if noticed.
4. They should remove the dormant accounts and enable 2-factor authentication.
The major focus should be on the security policy. During off-boarding, employers must hand over all the digital accounts and resources of the company to the Information Technology department and seek necessary practices to ensure that they haven’t got anything illegally along with them. Similarly, the company must ensure the worker that his personal information and dormant accounts are completely signed-out from the devices.

Read next: The Majority of Cyber Attacks in 2021 Targeted Educational and Government Institutions