Scammers have become so clever that they use various techniques to hack the data of users and they also want to have access to their devices that they are using. These cases have been increased a lot especially during the quarantine situation when more people have started working online. Recently, Microsoft has discovered a huge-scale business email compromise (BEC) campaign that has attacked more than 120 organizations with the help of typo-squatted domains, for those who do not know what typo-squatting is, it is like sitting on websites on someone else’s brand, also known as URL hijacking. These typo-squatted domains were registered a few days ago before being attacked.
These hackers use different types of techniques including usurping or phishing to compromise business email accounts, after that they use these data to send the payments to their controlled accounts of banks and they also try to make employees their prey by using the gift card scam. Microsoft company used the typo-squatted domain by delivering the emails, pretending to be managers of the company, to the employees from different industry sectors like professional services and real estate, etc.
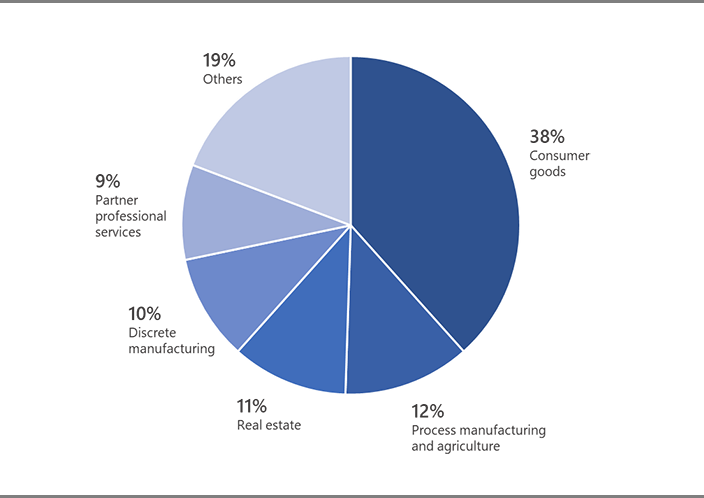
The threat intelligence group of Microsoft has pointed out this pattern by using incorrect TLD or a slightly wrong spelling the name of the company, just like a few weeks ago some hackers tried to a main almost same domain name like microsoft.com to microsoft.xyz or micrrosoft.com, etc. and they also tried to send the user an email to get their data. According to the report, 38% of the industry of consumer goods was targeted. However, even though, the exertions of attackers to match the fooled domain to the exact target, Microsoft said that the registered domains did not always associate with the organization being imitated in the email. Their method was imperfect at times, the attackers’ investigation skills are obvious since they tackled the targeted employees’ using the first names.
Microsoft has also discovered that attackers are using various tactics to make fake replies because that will create authenticity in an email, this way they can trap more employees. Microsoft further said that filling the headers while creating an email gives the authentic looks and that the scammer was simply responding to the prevailing email thread between the Yahoo and Outlook users. This trait sets this campaign apart from most BEC campaigns, where the scammer simply includes a genuine or specially created fake email by including the writer, recipient, and subject in the main part of the email, this will look like a new email was a reply to the prevailing email.
The methods of these BEC scammers do not look much sophisticated but still, these attacks make a huge financial loss each year, according to a report, $1.8 billion financial loss was caused because of these BEC attacks. The FBI has also given warnings to the corporate sector of the US that these attacks are increasing consistently.
Read next: Through 'Tip Jar' Twitter users can donate but this feature can leak the email address of users, which PayPal needs to resolve
These hackers use different types of techniques including usurping or phishing to compromise business email accounts, after that they use these data to send the payments to their controlled accounts of banks and they also try to make employees their prey by using the gift card scam. Microsoft company used the typo-squatted domain by delivering the emails, pretending to be managers of the company, to the employees from different industry sectors like professional services and real estate, etc.
The threat intelligence group of Microsoft has pointed out this pattern by using incorrect TLD or a slightly wrong spelling the name of the company, just like a few weeks ago some hackers tried to a main almost same domain name like microsoft.com to microsoft.xyz or micrrosoft.com, etc. and they also tried to send the user an email to get their data. According to the report, 38% of the industry of consumer goods was targeted. However, even though, the exertions of attackers to match the fooled domain to the exact target, Microsoft said that the registered domains did not always associate with the organization being imitated in the email. Their method was imperfect at times, the attackers’ investigation skills are obvious since they tackled the targeted employees’ using the first names.
Microsoft has also discovered that attackers are using various tactics to make fake replies because that will create authenticity in an email, this way they can trap more employees. Microsoft further said that filling the headers while creating an email gives the authentic looks and that the scammer was simply responding to the prevailing email thread between the Yahoo and Outlook users. This trait sets this campaign apart from most BEC campaigns, where the scammer simply includes a genuine or specially created fake email by including the writer, recipient, and subject in the main part of the email, this will look like a new email was a reply to the prevailing email.
The methods of these BEC scammers do not look much sophisticated but still, these attacks make a huge financial loss each year, according to a report, $1.8 billion financial loss was caused because of these BEC attacks. The FBI has also given warnings to the corporate sector of the US that these attacks are increasing consistently.
Read next: Through 'Tip Jar' Twitter users can donate but this feature can leak the email address of users, which PayPal needs to resolve